Enabling single sign-on with JumpCloud
Roles and permissions
Only administrators can enable SSO for the organization
Note
This feature is not supported in Hyperproof Gov.
Hyperproof supports single sign-on (SSO) with JumpCloud via SAML. Once SSO is enabled for your organization, users can log in to Hyperproof in one of two ways:
With their JumpCloud credentials using a custom URL specific to your organization.
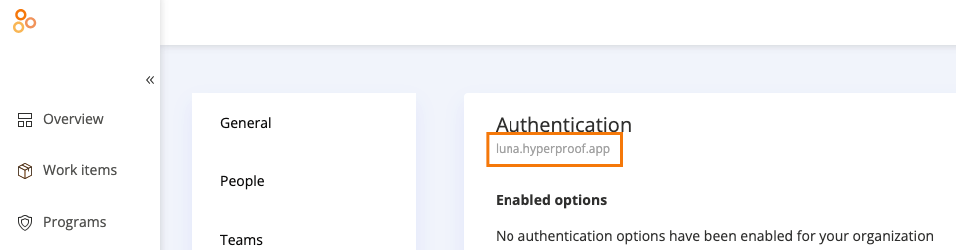
If your organization is in Hyperproof US, an example of a custom URL is:
https://luna.hyperproof.appIf your organization is in Hyperproof EU, an example of a custom URL is:
https://luna.hyperproof.eu
Via IdP-initiated sign-in, i.e., clicking the Hyperproof application on the JumpCloud Applications page. Note that IdP-initiated sign-in might pose a security risk and is therefore not turned on by default.
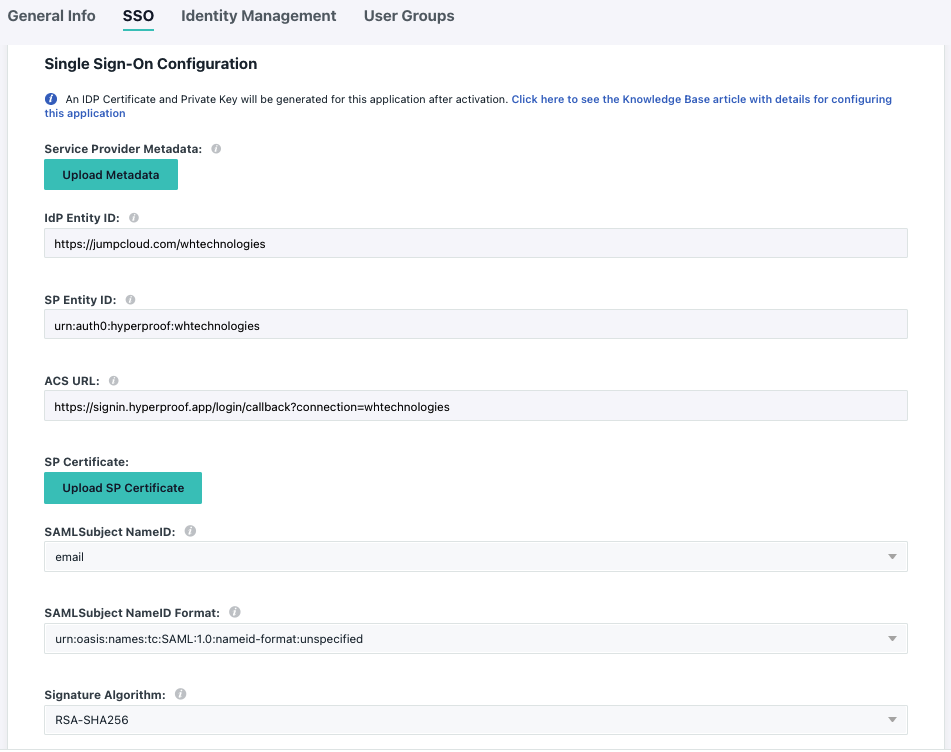
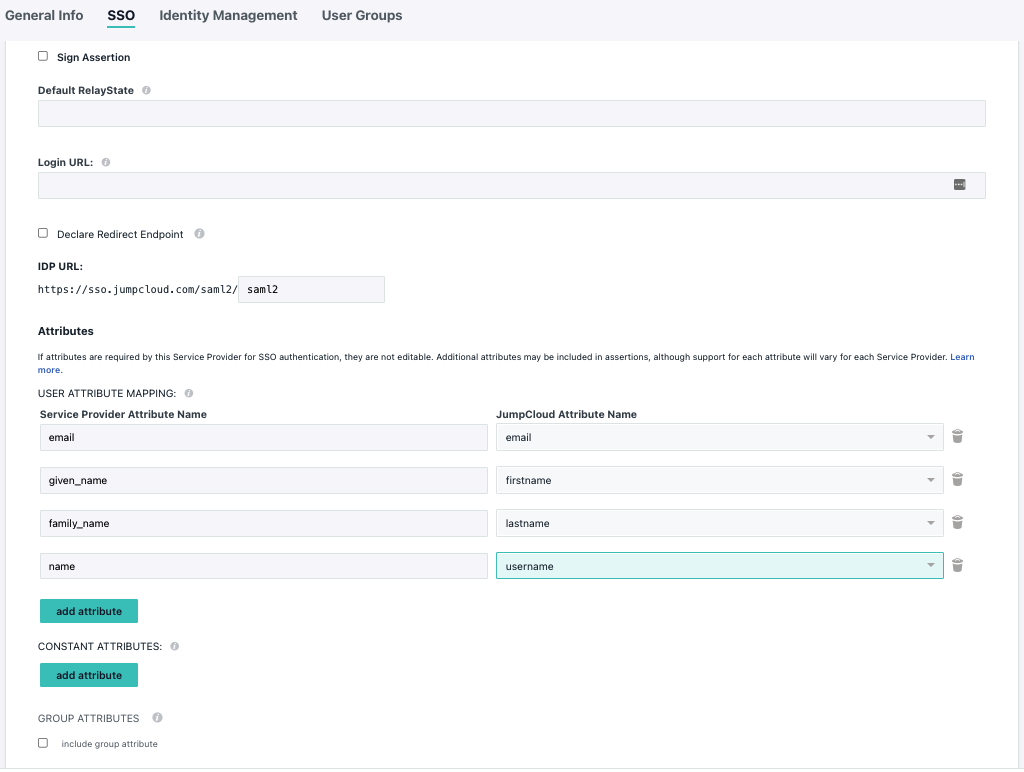
The first step towards enabling SSO in your organization is to add Hyperproof to your JumpCloud tenant. You’ll need a subdomain, which is provisioned by Hyperproof Support. To get your subdomain, create a support request asking for SSO setup.
Note
If the domain is a .com address, the subdomain is set as the domain without the .com suffix.
If the domain is not a .com address, the subdomain is set as the domain name without the period.
Examples
Domain name | Subdomain |
|---|---|
http://acme.com | acme |
http://lunabtechnologies.com | lunabtechnologies |
http://techstartup.io | techstartupio |
http://whitehouse.gov | whitehousegov |
Note
If you have SSO enabled and you invite someone to your organization whose email address is not part of your SSO domain, such as external auditors or contractors, they can't log into Hyperproof via the custom URL provided for SSO. These users must log in using the default URL for your Hyperproof instance. Default Hyperproof URLs include:
Hyperproof US: https://hyperproof.app/
Hyperproof EU: https://hyperproof.eu/
Hyperproof Gov: http://hyperproofgov.app/